Pentagon posts guidance on implementing zero trust for operational technology

The Defense Department recently published a new document outlining how organizations should apply zero-trust cybersecurity principles for operational technology systems.
Posted in November by the Pentagon’s chief information office, the guidance includes 105 zero-trust activities and capability outcomes to implement in operational technology (OT) environments — including 84 activities considered minimum “target levels” and 21 for “advanced levels” of zero trust. In addition, the list is divided across seven pillars: users; devices; applications and workloads; data; networks and environments; automation and orchestration; and visibility and analytics.
Zero trust is a cybersecurity concept that assumes networks are always compromised by adversaries, meaning the Pentagon must implement controls to consistently monitor and authenticate users and their devices.
The department has been working to adopt zero trust for its IT systems since 2022, but officials have previously stated that they planned to expand the effort to OT — broadly defined in the document as “programmable systems and devices that interact with the physical environment or manage devices that interact with the physical environment.”
As such, OT environments can include facility control systems, power grids, energy management systems, transportation systems and some elements of a weapon system or defense critical infrastructure component. For example, the controls can apply to a power source for a specific weapon, but not that system’s internal targeting or firing systems.
Furthermore, the Pentagon has divided the OT environment into two layers: an operational layer and a process control layer.
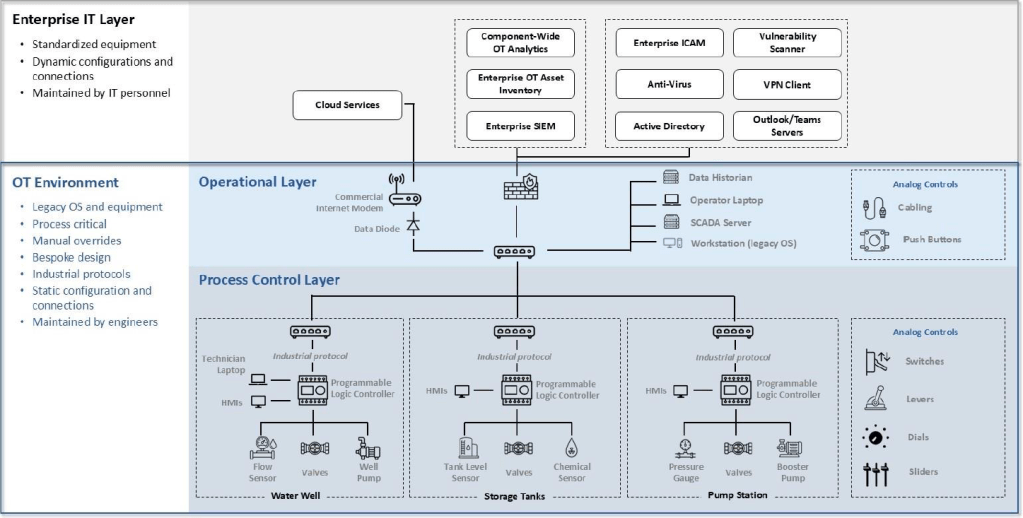
Because of the differences between IT and OT environments, different approaches must be taken to achieve zero trust for both. The new guidance specifically notes that OT systems often leverage legacy equipment and are operated by a high-specialized workforce with engineering expertise.
“While the core principles of [zero trust] — data protection, strong authentication, network segmentation, and threat monitoring — apply to OT, their implementation and deployment timescales require careful consideration of OT-specific constraints and priorities,” the document stated. “These challenges make [zero trust] adoption more difficult in OT environments and require modifications to the activities and outcomes.”
To account for these distinctions, the Pentagon’s new zero-trust guidance includes activities tailored specifically to challenges and requirements of operational technology systems. At the same time, the outcomes are closely aligned with those for IT systems.
“The commonality between the [zero trust] for IT and [zero trust] for OT guidance facilitates phased interoperability between the [zero trust] for IT and [zero trust] for OT implementations,” the guidance noted. “For example, credentialing, asset management, threat detection, actor role and attribution, and behavioral analytics may be initially installed locally within the OT environment; they will eventually be integrated with the comparable Enterprise IT tools and standards to provide a common approach across a Component and the [Defense Department] at large.”
While Pentagon components must reach target levels of zero trust for their IT systems by the end of fiscal 2027, the new document does not give a concrete deadline for OT environments.
The department intends to publish an updated Zero Trust Strategy in early 2026 and develop additional guidance for both weapon systems and defense critical infrastructure.






